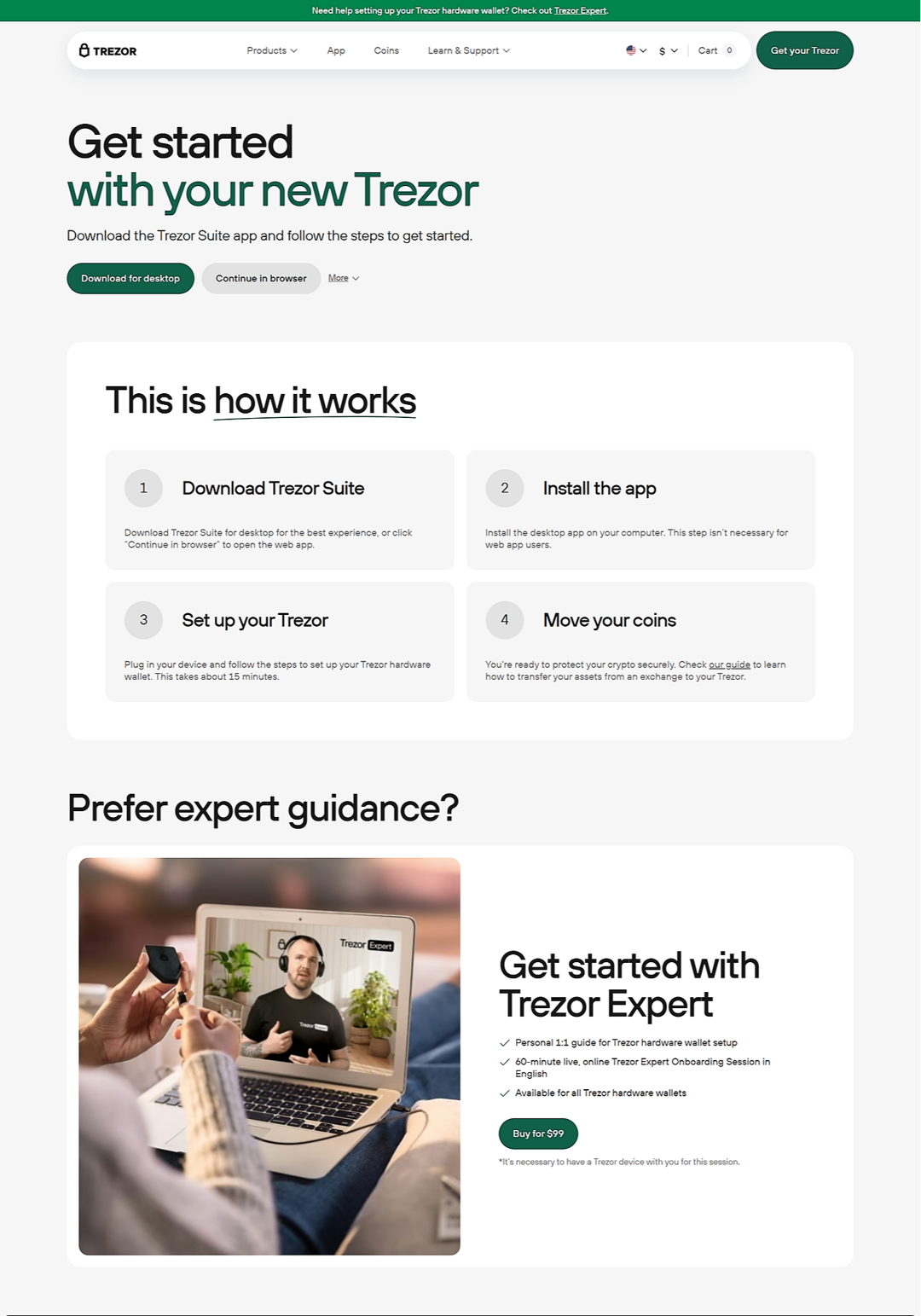
Trezor Login: Your Secure Gateway to Crypto Access
The Trezor Login process is the first and most important step toward accessing your digital assets safely. Whether you’re managing Bitcoin, Ethereum, or other cryptocurrencies, Trezor Login ensures your connection is secure, private, and fully protected against online threats.
Why the Trezor Login Experience Prioritizes Security
What makes Trezor Login unique is its offline verification method. Your private keys never touch the internet, and during Trezor Login, your device performs critical authentication locally. This reduces exposure and eliminates many risks associated with centralized logins.
How Trezor Login Works with Trezor Suite
Using Trezor Login through Trezor Suite connects you to an intuitive dashboard for managing your assets. After you complete Trezor Login, you can buy, exchange, and monitor your portfolio — all while knowing your keys remain under your control.
Trezor Login and Two-Factor Security
With Trezor Login, two-factor authentication is physical. Your hardware device becomes your second factor, making Trezor Login inherently more secure than SMS or app-based codes. This physical confirmation keeps phishing attempts at bay.
The Simplicity of the Trezor Login Flow
One of the strengths of Trezor Login is how user-friendly it is. After plugging in your device, Trezor Login takes just a few steps: launch Trezor Suite, verify on your screen, and you’re ready to go. It’s fast, easy, and intuitive.
- Open Trezor Suite to initiate Trezor Login
- Connect your Trezor Model T or One device
- Review and approve the Trezor Login prompt on your device
- Access your dashboard securely
- Manage your crypto portfolio after Trezor Login is complete
Trezor Login and Passphrase Protection
For advanced users, Trezor Login can be combined with a passphrase for extra protection. With this feature, your Trezor Login experience adds a hidden wallet layer, making unauthorized access virtually impossible — even if your device is stolen.
Common Issues During Trezor Login and How to Solve Them
If you ever face trouble during Trezor Login, it’s usually related to firmware updates, browser compatibility, or USB connections. Refreshing the Trezor Bridge, restarting your browser, or switching USB ports often resolves Trezor Login problems quickly.
Trezor Login Across Multiple Devices
You can use Trezor Login on any device where Trezor Suite is supported. Whether you’re on a desktop at home or a laptop while traveling, Trezor Login keeps your assets secure no matter where you go — without storing your credentials online.
Trezor Login Integration with Third-Party Wallets
Some decentralized apps and web wallets now support Trezor Login directly. For example, when accessing dApps or using services like MetaMask with hardware support, Trezor Login provides a trusted authentication path while maintaining self-custody.
The Future of Crypto Safety Lies in Trezor Login
As the industry shifts toward self-custody, the role of Trezor Login becomes even more vital. Centralized exchanges may offer convenience, but Trezor Login ensures that only you hold the keys, empowering you to be your own bank.
Why Beginners Should Start with Trezor Login
Even if you’re brand new to crypto, starting with Trezor Login is a smart choice. It simplifies wallet setup, reduces the risk of online hacks, and guides you through safe practices. With Trezor Login, you’re building the habit of security from the very beginning.
Conclusion: Trezor Login is the First Step to Full Control
Whether you're a seasoned investor or a curious beginner, Trezor Login is your gateway to self-sovereign crypto management. It’s simple, secure, and designed with your safety in mind. By trusting Trezor Login, you're choosing to keep your assets exactly where they belong — under your control.
Made in Typedream